- (Exam Topic 3)
A security analyst sees the following OWASP ZAP output from a scan that was performed against a modern version of Windows while testing for client-side vulnerabilities:
Which of the following is the MOST likely solution to the listed vulnerability?
Correct Answer:
D
- (Exam Topic 2)
A security analyst is auditing firewall rules with the goal of scanning some known ports to check the firewall’s behavior and responses. The analyst executes the following commands: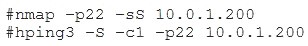
The analyst then compares the following results for port 22: nmap returns “Closed”
hping3 returns “flags=RA”
Which of the following BEST describes the firewall rule?
Correct Answer:
B
No doubt does the nmap result mean its being rejected as it returns closed. However, what threw me for a loop was the hping3 response. After further web surfing I found that the "flag=RA" means actually means "flag= RST, ACK" which means that it too was rejected.
- (Exam Topic 1)
A team of security analysts has been alerted to potential malware activity. The initial examination indicates one of the affected workstations is beaconing on TCP port 80 to five IP addresses and attempting to spread across the network over port 445. Which of the following should be the team’s NEXT step during the detection phase of this response process?
Correct Answer:
D
- (Exam Topic 3)
A security analyst identified some potentially malicious processes after capturing the contents of memory from a machine during incident response. Which of the following procedures is the NEXT step for further in investigation?
Correct Answer:
C
- (Exam Topic 1)
A security analyst is reviewing the following web server log: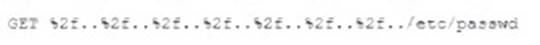
Which of the following BEST describes the issue?
Correct Answer:
A