Refer to the exhibit.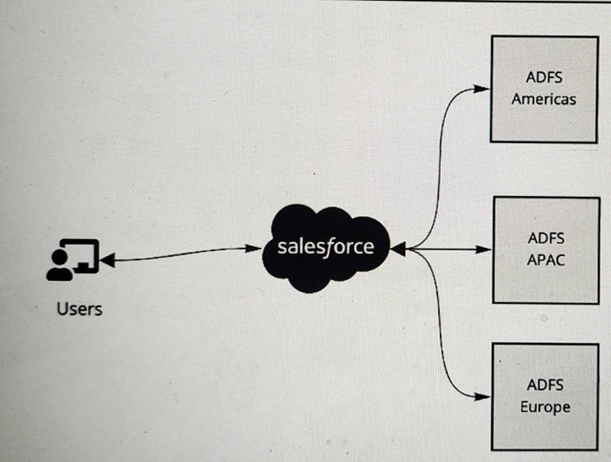
A multinational company is looking to rollout Salesforce globally. The company has a Microsoft Active Directory Federation Services (ADFS) implementation for the Americas, Europe and APAC. The company plans to have a single org and they would like to have all of its users access Salesforce using the ADFS . The company would like to limit its investments and prefer not to procure additional applications to satisfy the requirements.
What is recommended to ensure these requirements are met ?
Correct Answer:
B
To have all of its user’s access Salesforce using the ADFS, the multinational company should implement Identity Connect to provide single sign-on to Salesforce and federate across multiple ADFS systems. Identity Connect is a tool that synchronizes user data between Microsoft Active Directory and Salesforce. It allows single sign-on and federation between multiple Active Directory domains and a single Salesforce org. Identity Connect can also handle user provisioning and deprovisioning based on the changes made in Active Directory. The other options are not recommended for this scenario, as they either require additional applications, do not support federation, or do not provide a seamless user experience. References: Identity Connect Implementation Guide, Identity Connect Overview
Universal containers (UC) is setting up Delegated Authentication to allow employees to log in using their corporate credentials. UC's security team is concerned about the risk of exposing the corporate login service on the Internet and has asked that a reliable trust mechanism be put in place between the login service and salesforce. What mechanism should an architect put in place to enable a trusted connection between the login services and salesforce?
Correct Answer:
D
To enable a trusted connection between the login services and Salesforce, UC should enforce mutual authentication between systems using SSL. Mutual authentication is a process in which both parties in a communication verify each other’s identity using certificates7. SSL (Secure Sockets Layer) is a protocol that provides secure communication over the Internet using encryption and certificates8. By using mutual authentication with SSL, UC can ensure that only authorized login services can access Salesforce and vice versa. This can prevent unauthorized access, impersonation, or phishing attacks.
References: Mutual Authentication, SSL (Secure Sockets Layer)
Universal Containers uses Salesforce as an identity provider and Concur as the Employee Expense management system. The HR director wants to ensure Concur accounts for employees are created only after the apocopate approval in the Salesforce org.
Which three steps should the identity architect use to implement this requirement? Choose 3 answers
Correct Answer:
BCE
User provisioning is a feature that allows Salesforce to create, update, or deactivate user accounts on a
third-party system, such as Concur, based on user assignments in Salesforce1. To implement user provisioning for Concur with an approval process, the identity architect should use the following steps2: Create a connected app for Concur in Salesforce. A connected app is an application that integrates with Salesforce using APIs and standard protocols, such as SAML, OAuth, and OpenID Connect3. To create a connected app for Concur, you need to provide the basic information, such as the app name, logo URL, contact email, and API name. You also need to enable SAML and configure the SAML settings, such as the entity ID, ACS URL, and subject type4.
Create a connected app for Concur in Salesforce. A connected app is an application that integrates with Salesforce using APIs and standard protocols, such as SAML, OAuth, and OpenID Connect3. To create a connected app for Concur, you need to provide the basic information, such as the app name, logo URL, contact email, and API name. You also need to enable SAML and configure the SAML settings, such as the entity ID, ACS URL, and subject type4. Enable User Provisioning for the connected app. This step allows you to configure the user provisioning settings for the connected app, such as the provisioning API endpoint URL, the client ID and client secret, the mapping of user attributes, and the linkage rules5. You can also choose to require an approval process for user provisioning requests by selecting the Approval Required option6.
Enable User Provisioning for the connected app. This step allows you to configure the user provisioning settings for the connected app, such as the provisioning API endpoint URL, the client ID and client secret, the mapping of user attributes, and the linkage rules5. You can also choose to require an approval process for user provisioning requests by selecting the Approval Required option6. Create an approval process for UserProvisioningRequest object associated with the provisioning flow. A UserProvisioningRequest object represents a user provisioning request that is sent to or received from a third-party system7. An approval process specifies the steps necessary for a record to be approved and who must approve it at each step8. To create an approval process for UserProvisioningRequest object, you need to define the approval steps, assignees, actions, criteria, and email alerts9.
Create an approval process for UserProvisioningRequest object associated with the provisioning flow. A UserProvisioningRequest object represents a user provisioning request that is sent to or received from a third-party system7. An approval process specifies the steps necessary for a record to be approved and who must approve it at each step8. To create an approval process for UserProvisioningRequest object, you need to define the approval steps, assignees, actions, criteria, and email alerts9.
References: User Provisioning for Connected Apps
User Provisioning for Connected Apps Tutorial: Configure Salesforce for automatic user provisioning
Tutorial: Configure Salesforce for automatic user provisioning  Connected Apps
Connected Apps Create a Connected App
Create a Connected App Enable User Provisioning for a Connected App
Enable User Provisioning for a Connected App Require Approvals for User Provisioning Requests
Require Approvals for User Provisioning Requests  UserProvisioningRequest
UserProvisioningRequest Approval Processes
Approval Processes Create an Approval Process
Create an Approval Process
Universal containers (UC) is concerned that having a self-registration page will provide a means for "bots" or unintended audiences to create user records, thereby consuming licences and adding dirty data. Which two actions should UC take to prevent unauthorised form submissions during the self-registration process? Choose 2 answers
Correct Answer:
CD
To prevent unauthorized form submissions during the self-registration process, UC should require a captcha at the end of the self-registration process and use hidden fields populated via JavaScript events in the self-registration page. These methods will help to verify that the user is a human and not a bot, and also to validate the user’s input against some predefined values. Option A is not a good choice because open-ended security questions and complex password requirements may frustrate the user and reduce the conversion rate. Option B is not a good choice because lookup and picklist fields may not prevent bots from submitting the form, as they can be easily automated or bypassed.
References: Single Sign-On Implementation Guide, Customizing User Authentication with Login Flows
Universal containers want to build a custom mobile app connecting to salesforce using Oauth, and would like to restrict the types of resources mobile users can access. What Oauth feature of Salesforce should be used to achieve the goal?
Correct Answer:
D
The OAuth feature of Salesforce that should be used to restrict the types of resources mobile users can access is scopes. Scopes are parameters that specify the level of access that the mobile app requests from Salesforce when it obtains an OAuth token. Scopes can be used to limit the access to certain resources or actions, such as API calls, full access, web access, or refresh token. By configuring scopes in the connected app settings, Universal Containers can control what the mobile app can do with the OAuth token and protect against unauthorized or excessive access.
References: [OAuth Scopes], [Connected Apps], [OAuth Authorization Flows]