An OT supervisor has configured LDAP and FSSO for the authentication. The goal is that all the users be authenticated against passive authentication first and, if passive authentication is not successful, then users should be challenged with active authentication.
What should the OT supervisor do to achieve this on FortiGate?
Correct Answer:
D
Refer to the exhibit.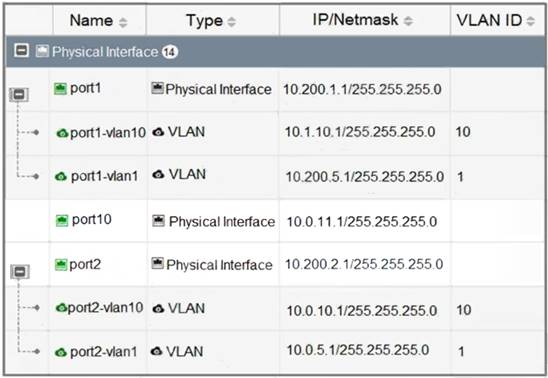
Which statement about the interfaces shown in the exhibit is true?
Correct Answer:
D
Refer to the exhibit.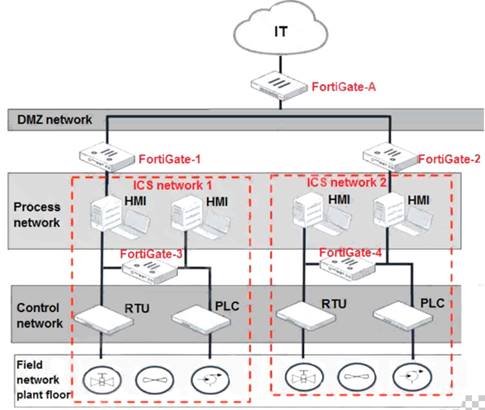
Based on the topology designed by the OT architect, which two statements about implementing OT security are true? (Choose two.)
Correct Answer:
CD
As an OT administrator, it is important to understand how industrial protocols work in an OT network. Which communication method is used by the Modbus protocol?
Correct Answer:
D
You are investigating a series of incidents that occurred in the OT network over past 24 hours in FortiSIEM. Which three FortiSIEM options can you use to investigate these incidents? (Choose three.)
Correct Answer:
CDE