After gaining access to a Linux system with a non-privileged account, a penetration tester identifies the following file: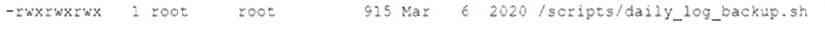
Which of the following actions should the tester perform FIRST?
Correct Answer:
B
A penetration tester has established an on-path position between a target host and local network services but has not been able to establish an on-path position between the target host and the Internet. Regardless, the tester would like to subtly redirect HTTP connections to a spoofed server IP. Which of the following methods would BEST support the objective?
Correct Answer:
D
A penetration tester utilized Nmap to scan host 64.13.134.52 and received the following results: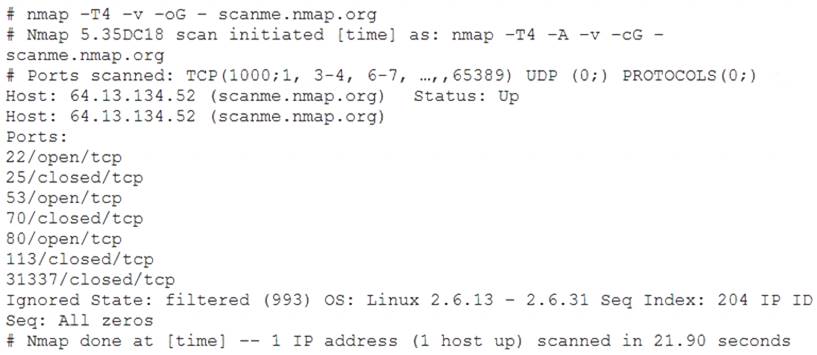
Based on the output, which of the following services are MOST likely to be exploited? (Choose two.)
Correct Answer:
BD
A penetration tester uncovers access keys within an organization's source code management solution. Which of the following would BEST address the issue? (Choose two.)
Correct Answer:
AE
Access keys are credentials that allow users to authenticate and authorize requests to a source code management (SCM) system, such as GitLab or AWS. Access keys should be kept secret and not exposed in plain text within the source code, as this can compromise the security and integrity of the SCM system and its data.
Some possible options for addressing the issue of access keys within an organization’s SCM solution are: Setting up a secret management solution for all items in the SCM system: This is a tool or service that securely stores, manages, and distributes secrets such as access keys, passwords, tokens, certificates,
Setting up a secret management solution for all items in the SCM system: This is a tool or service that securely stores, manages, and distributes secrets such as access keys, passwords, tokens, certificates,
etc. A secret management solution can help prevent secrets from being exposed in plain text within the
source code or configuration files3456. Developing a secure software development life cycle (SDLC) process for committing code to the SCM system: This is a framework or methodology that defines how software is developed, tested, deployed, and maintained. A secure SDLC process can help ensure that best practices for security are followed throughout the software development process, such as code reviews, static analysis tools, vulnerability scanning tools, etc. A secure SDLC process can help detect and prevent access keys from being included in the source code before they are committed to the SCM system1.
Developing a secure software development life cycle (SDLC) process for committing code to the SCM system: This is a framework or methodology that defines how software is developed, tested, deployed, and maintained. A secure SDLC process can help ensure that best practices for security are followed throughout the software development process, such as code reviews, static analysis tools, vulnerability scanning tools, etc. A secure SDLC process can help detect and prevent access keys from being included in the source code before they are committed to the SCM system1.
Which of the following provides a matrix of common tactics and techniques used by attackers along with recommended mitigations?
Correct Answer:
C