- (Exam Topic 3)
What are two recommended approaches to stop DNS tunneling for data exfiltration and command and control call backs? (Choose two.)
Correct Answer:
CE
- (Exam Topic 3)
How does Cisco Workload Optimization Manager help mitigate application performance issues?
Correct Answer:
B
Reference:
https://www.cisco.com/c/dam/en/us/solutions/collateral/data-center-virtualization/one-enterprisesuite/solution-o
- (Exam Topic 2)
Refer to the exhibit.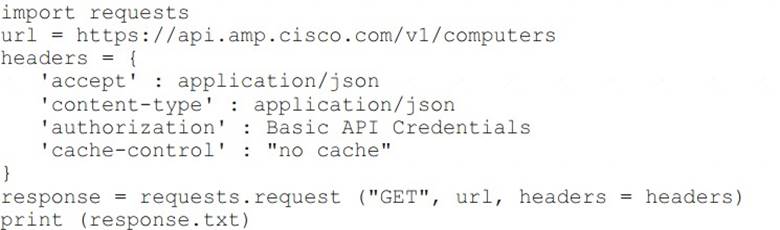
What will happen when this Python script is run?
Correct Answer:
D
Reference:
https://api-docs.amp.cisco.com/api_actions/details?api_action=GET+/v1/computers&api_host=api.apjc.
- (Exam Topic 3)
Which type of DNS abuse exchanges data between two computers even when there is no direct connection?
Correct Answer:
D
Reference: https://www.netsurion.com/articles/5-types-of-dns-attacks-and-how-to-detect-them
- (Exam Topic 3)
A network engineer must configure a Cisco ESA to prompt users to enter two forms of information before gaining access The Cisco ESA must also join a cluster machine using preshared keys What must be configured to meet these requirements?
Correct Answer:
A