- (Exam Topic 1)
What are the two most commonly used authentication factors in multifactor authentication? (Choose two)
Correct Answer:
AD
Reference: https://www.cisco.com/c/en/us/products/security/what-is-multi-factor-authentication.htmlThe two most popular authentication factors are knowledge and inherent (including biometrics like fingerprint,face, and retina scans. Biometrics is used commonly in mobile devices).
- (Exam Topic 3)
What is a description of microsegmentation?
Correct Answer:
A
- (Exam Topic 3)
An engineer is adding a Cisco DUO solution to the current TACACS+ deployment using Cisco ISE. The engineer wants to authenticate users using their account when they log into network devices. Which action accomplishes this task?
Correct Answer:
B
- (Exam Topic 3)
Which two parameters are used for device compliance checks? (Choose two.)
Correct Answer:
CE
- (Exam Topic 2)
Drag and drop the descriptions from the left onto the correct protocol versions on the right.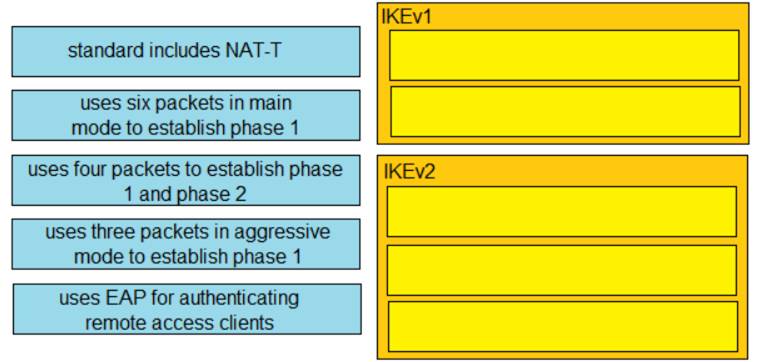
Solution:
Graphical user interface Description automatically generated with low confidence
Does this meet the goal?
Correct Answer:
A