- (Exam Topic 4)
You have an Azure subscription that contains the Azure Log Analytics workspaces shown in the following table.
You create the virtual machines shown in the following table.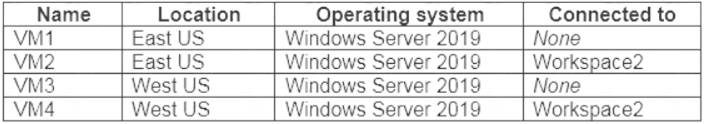
You plan to use Azure Sentinel to monitor Windows Defender Firewall on the virtual machines. Which virtual machines you can connect to Azure Sentinel?
Correct Answer:
D
Reference:
https://docs.microsoft.com/en-us/azure/sentinel/connect-windows-firewall
- (Exam Topic 4)
You have an Azure subscription that contains the key vaults shown in the following table.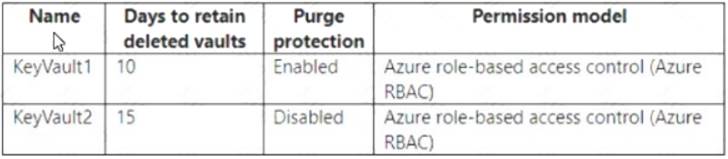
The subscription contains the users shown in the following table.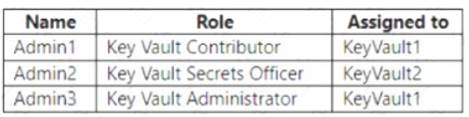
On June 1, you perform the following actions:
• Delete a key named key1 from KeyVault1.
• Delete a secret named secret 1 from KeyVault2.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.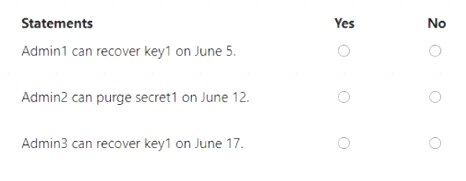
Solution:
Yes Yes No
Does this meet the goal?
Correct Answer:
A
- (Exam Topic 4)
Your company has an Azure subscription named Sub1 that is associated to an Azure Active Directory Azure (Azure AD) tenant named contoso.com.
The company develops a mobile application named App1. App1 uses the OAuth 2 implicit grant type to acquire Azure AD access tokens.
You need to register App1 in Azure AD.
What information should you obtain from the developer to register the application?
Correct Answer:
A
For Native Applications you need to provide a Redirect URI, which Azure AD will use to return token
responses. References:
https://docs.microsoft.com/en-us/azure/active-directory/develop/v1-protocols-oauth-code
- (Exam Topic 4)
You have 10 virtual machines on a single subnet that has a single network security group (NSG). You need to log the network traffic to an Azure Storage account.
Which two actions should you perform? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
Correct Answer:
D
A network security group (NSG) enables you to filter inbound traffic to, and outbound traffic from, a virtual machine (VM). You can log network traffic that flows through an NSG with Network Watcher's NSG flow log
capability. Steps include: Create a VM with a network security group
Create a VM with a network security group Enable Network Watcher and register the Microsoft.Insights provider
Enable Network Watcher and register the Microsoft.Insights provider Enable a traffic flow log for an NSG, using Network Watcher's NSG flow log capability
Enable a traffic flow log for an NSG, using Network Watcher's NSG flow log capability  Download logged data
Download logged data View logged data Reference:
View logged data Reference:
https://docs.microsoft.com/en-us/azure/network-watcher/network-watcher-nsg-flow-logging-portal
- (Exam Topic 1)
You need to deploy AKS1 to meet the platform protection requirements.
Which four actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
NOTE: More than one order of answer choices is correct. You will receive credit for any of the correct orders you select.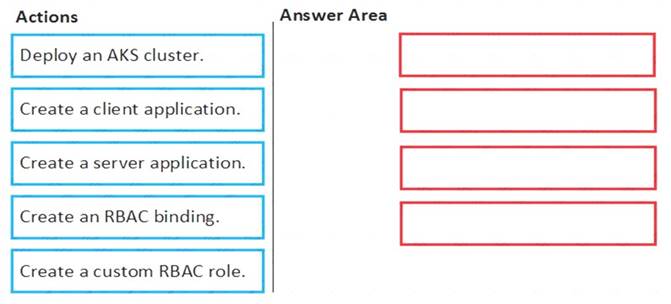
Solution:
Scenario: Azure AD users must be to authenticate to AKS1 by using their Azure AD credentials. Litewire plans to deploy AKS1, which is a managed AKS (Azure Kubernetes Services) cluster. Step 1: Create a server application
To provide Azure AD authentication for an AKS cluster, two Azure AD applications are created. The first
application is a server component that provides user authentication. Step 2: Create a client application
The second application is a client component that's used when you're prompted by the CLI for authentication. This client application uses the server application for the actual authentication of the credentials provided by the client.
Step 3: Deploy an AKS cluster.
Use the az group create command to create a resource group for the AKS cluster. Use the az aks create command to deploy the AKS cluster.
Step 4: Create an RBAC binding.
Before you use an Azure Active Directory account with an AKS cluster, you must create role-binding or cluster role-binding. Roles define the permissions to grant, and bindings apply them to desired users. These assignments can be applied to a given namespace, or across the entire cluster.
Reference:
https://docs.microsoft.com/en-us/azure/aks/azure-ad-integration
Does this meet the goal?
Correct Answer:
A